Introduction
OP AutoClicker is one of the most popular auto clickers for windows, it’s almost always the first result for auto clickers on google, as well as being really easy to use. I downloaded it from here. I would highly recommend doing the same if you are going to download it.
File hash
File hashes allow you to compare 2 files, even if their name changes, based on the contents of the file. The SHA256 hash of the copy I downloaded was the following:
|
|
I used the PowerShell command below to calculate it:
|
|
If you calculate the file hash and it is different, then it means you have a different file to me, this can mean you have an older version, a newer version, or a compromised version.
Safe file hashes
|
|
My copy
For reference, the copy I downloaded looks like this when I run it:
How I tested it
These methods of testing aren’t perfect, it is still possible that even with both of the tests below it might contain malicious code.
VirusTotal
VirusTotal allows for 72 different virus scanners to attempt to detect any viruses in a file, each by checking their databases for malicious files, and it also tags each file with different behaviours, such as checks-user-input, checks-disk-space. It is extremely common for at least 1 of the scans to report that it contains malicious code even if it is a harmless file.
Running the scan
Firstly, I uploaded the file to VirusTotal to check for any obvious signs of a virus, on this page 1/72 of the scans detected anything, meaning that it is likely that the scan that detected something flagged a false positive.
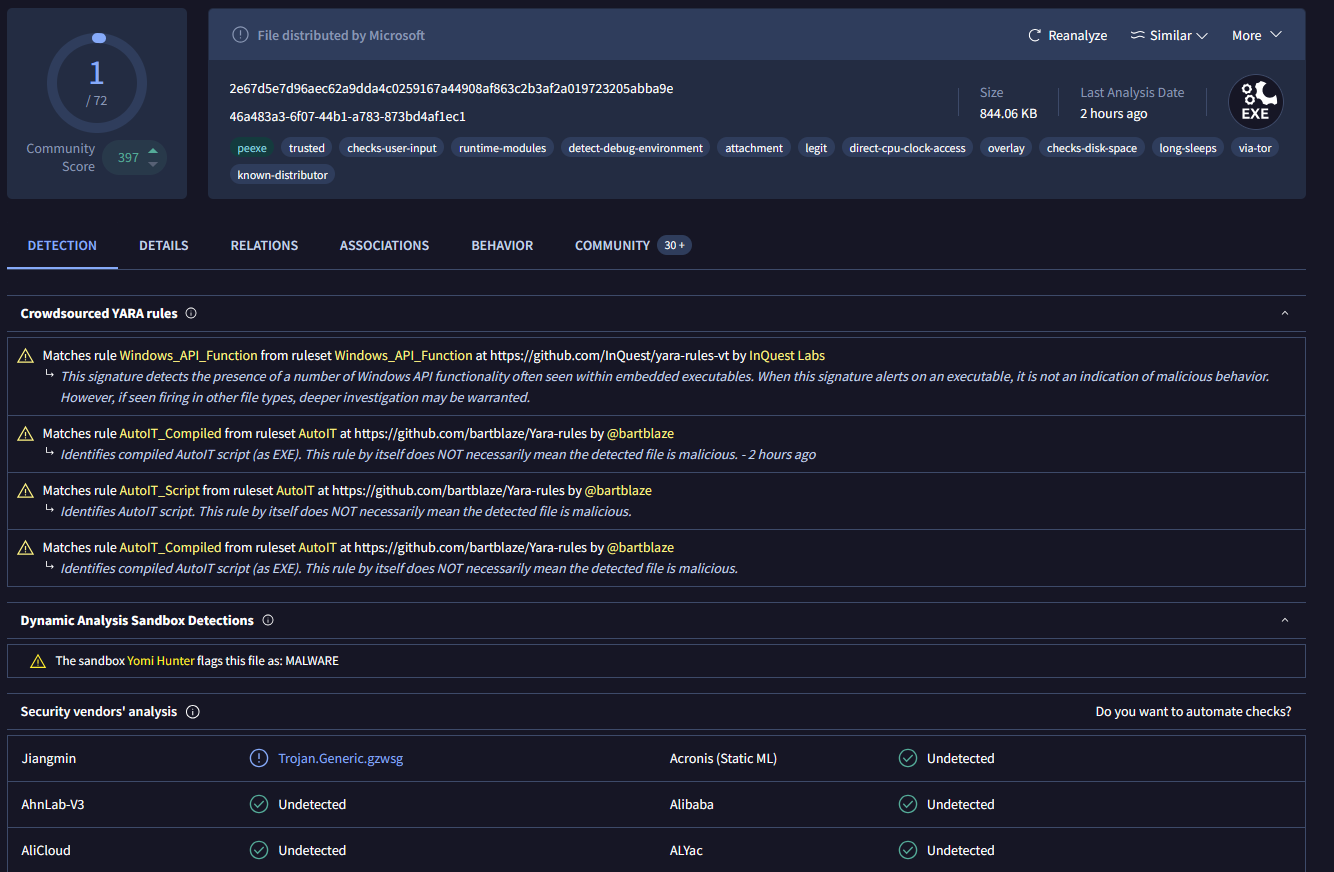 Here is a link to the VirusTotal scan: https://www.virustotal.com/gui/file/2e67d5e7d96aec62a9dda4c0259167a44908af863c2b3af2a019723205abba9e
Here is a link to the VirusTotal scan: https://www.virustotal.com/gui/file/2e67d5e7d96aec62a9dda4c0259167a44908af863c2b3af2a019723205abba9e
Triage
Triage is an online sandbox designed for checking malicious files to see what they do. It also rates files out of 10 for how malicious they are. It detects if programs perform various actions such as grabbing browser secrets, changing the registry and more.
Running the scan
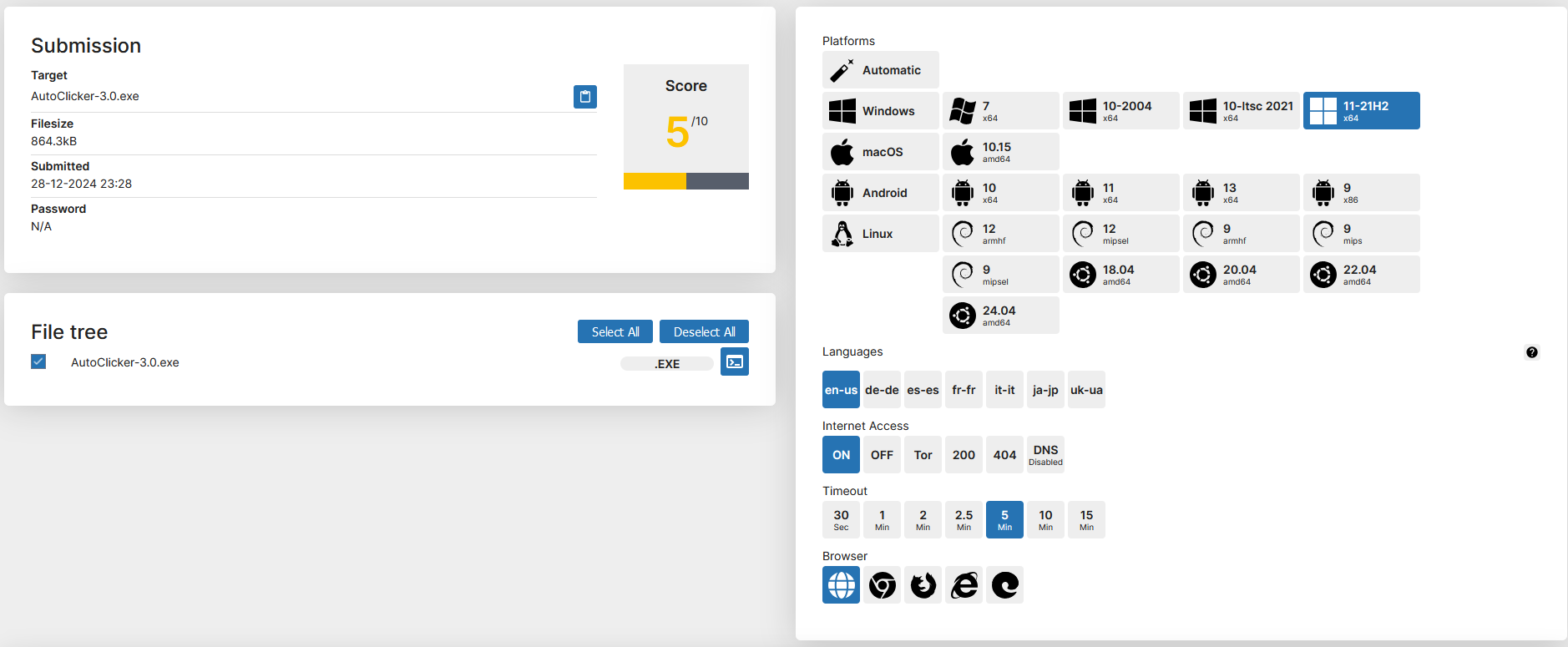
First, I uploaded the file to Triage, and it reported a 5/10 score, meaning that it thinks it’s slightly malicious, but not dangerous. Below are the settings I used when uploading:
 Once I ran the scan it reported the following behaviours:
Once I ran the scan it reported the following behaviours:
- Enumerates physical storage devices (Attempts to interact with connected storage/optical drives)
- System Location Discovery: System Language Discovery (Attempt gather information about the system language of a victim in order to infer the geographical location of that host)
- Suspicious behaviour: GetForegroundWindowSpam Of these behaviours, the only one I don’t quite understand is the first one, although I’m sure there’s a good reason for it. The second one is likely in order for it to be able to localise the interface to work on different languages (Not 100% sure about it). And finally the 3rd one is likely it checking if it is currently in the foreground for some reason. The score also updated once it has run in Triage, now becoming a 3/10 instead of a 5/10.
Re-running the scan
I decided to re-run the scan whilst using it for even longer, this time the new score remained the same (3/10), but the signatures did change a little bit, now having 3 new signatures:
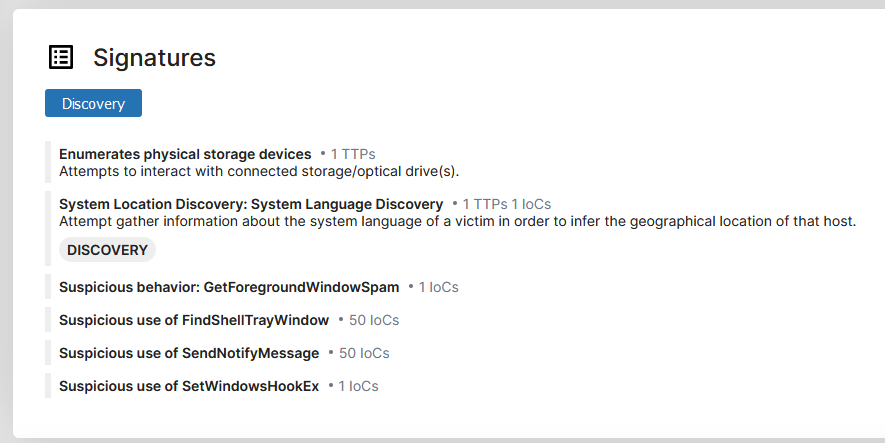 Overall, these are still likely harmless, as they are pretty basic functions of windows. Triage would show if it attempted to access the registry, or if it tried to change any settings.
Overall, these are still likely harmless, as they are pretty basic functions of windows. Triage would show if it attempted to access the registry, or if it tried to change any settings.
Link to triage: here On that link it is possible to view signatures, my configuration as well as the replay of how I tested it.
Packet Capture
From the Triage test I downloaded the packed capture in order to check for anything malicious, and below are the results.
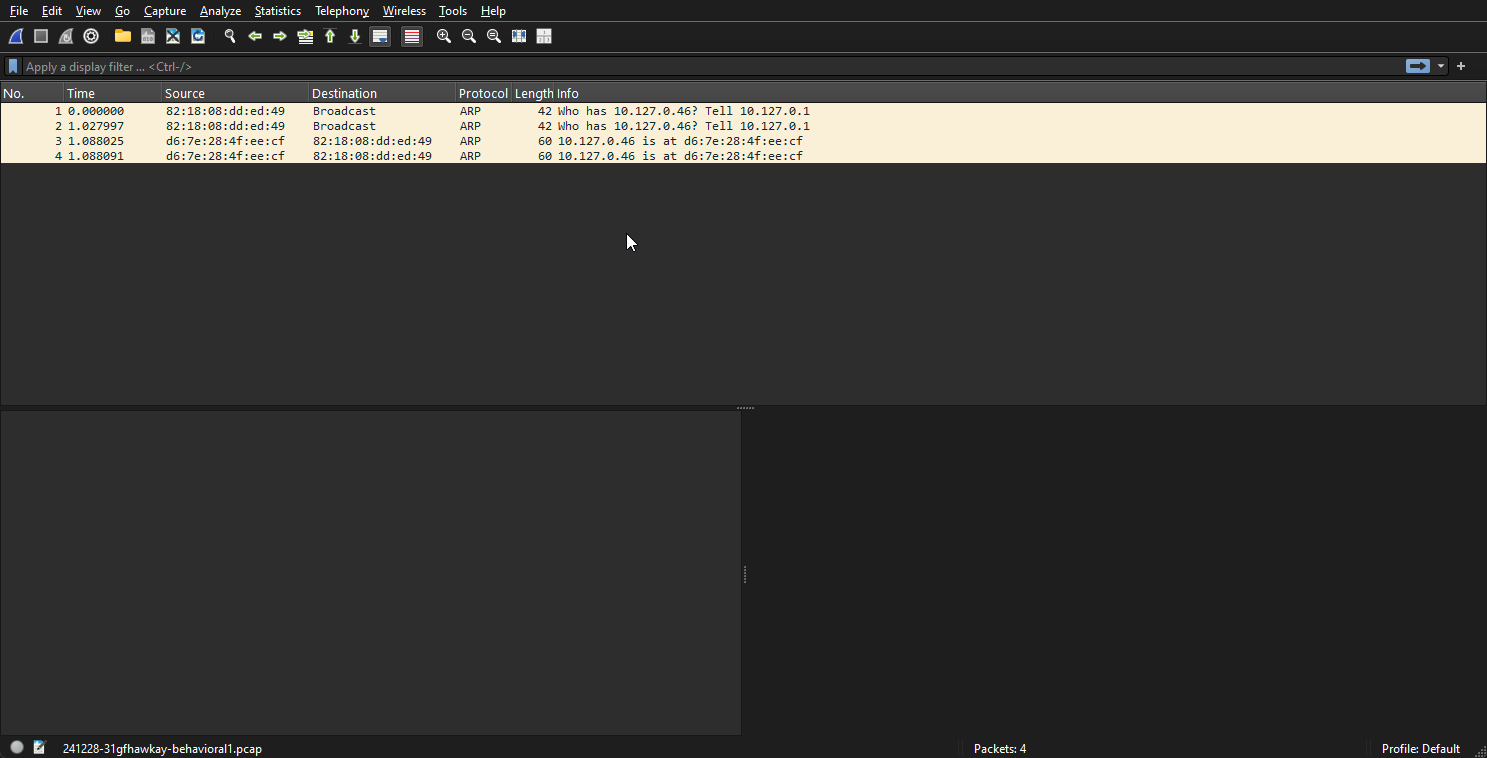 This is just a simple network discovery request, likely from windows or similar. It is unlikely that the program is making this request.
This is just a simple network discovery request, likely from windows or similar. It is unlikely that the program is making this request.
Download the file
If you would like to download the file, I would highly recommend downloading it from here. As far as I can tell this is the only official download, not including the one from the Microsoft store. CurseForge also scans for malware, or at least claims to.
Why it is safe
It seems to perform only the actions it needs to, such as interacting with the cursor. It does have some other signatures but those could be bad detections, or simply bad programming. It also looks to not attempt to access any credentials, such as browser cookies, which is important. The “safety” of this program does depend on when you download it, so if the creator updates it, then it might not necessarily be safe.
Why you need to be careful
Widely installed applications such as this one (Over 1 million downloads during the week of writing), are a prime target for scammers and other malicious actors, if they can find a way to use popular apps to steal information or run malicious code then they will try. Apps with a single developer are also slightly risky as it is easy for them to be manipulated into uploading a malicious version of their file.
Information about testing
My testing isn’t entirely conclusive, I could have missed something even though I did try to make sure that every aspect was checked. I have personally been using this autoclicker for over 5 years, and I haven’t had any problems but it is still possible that I got lucky and didn’t download a malicious version. Both VirusTotal and Triage aren’t conclusive ways to tell if a file is a virus or not, they only serve as indicators.
Conclusion
If your file hash matches the same one I mentioned at the start of this post then I would trust it, otherwise I would take caution. I will keep this blog post updated if I re-test newer versions of this OP AutoClicker and put their file-hashes near the top of this post. If you are in doubt, then try to find an alternative, this post only serves it’s purpose if you, the reader, have trust in my testing.
TL;DR
OP AutoClicker 3.0 can be trusted if your file hash matches the one at the start of this post. If it doesn’t then take caution.